Encrypted Files and Engines Memberships Groups |
Once encrypted, the files are organized into groups that belong to the encryption engine used. A complete overview of this structure is accessible in the section of the main window called Encrypted Files, where you can make selections for the group membership.
Speedcrypt does everything it can to make the task of its users easy. Specifically, it creates well-organized archives through which you can select the files to be decrypted, all in a very pleasant and equally intuitive graphical context.
This section of the main page allows you to Decrypt Files completely independently of the Windows Shell. All the file import rules described in the Add Files section of this Online Guide under the Entry Mode paragraph still apply.
The section is divided into two panels. On the left is the panel containing the encryption engines used by Speedcrypt and the groups of associated files based on the encryption process. Note that each group of files is represented by a Master Key, so the number of groups equals the number of processes and Master Keys used. The panel on the right contains the grid with the list of encrypted files. Each time you select a group, the status bar displays the number of associated files and the overall size in KB.
As mentioned before, the hierarchical organization of encrypted files into groups and subgroups allows for quick identification of the files and the creation of a decryption list in a very short time. All of this is done within the program, without relying on the Windows Shell, and it also ensures a consistently organized and easily accessible structure. All of this is achieved through a visually pleasing and intuitive graphical interface.
For each cryptographic process, Speedcrypt organizes a related archive and a group based on the engine used. As previously explained, the groups are composed in the appropriate panel within a numerical hierarchical structure. This structure will be automatically updated after each process, linking the new groups to the encryption engine and updating the total number of processes. Let's now take a closer look at the hierarchical structure in which the groups are composed:
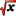 ENGINES: Parent Node. Contains child nodes
ENGINES: Parent Node. Contains child nodes ENGINES-AES-GCM: Child Node. Contains groups
ENGINES-AES-GCM: Child Node. Contains groups ENGINES-AES-RIJNDAEL: Child Node. Contains groups
ENGINES-AES-RIJNDAEL: Child Node. Contains groups ENGINES-PGP: Child Node. Contains group
ENGINES-PGP: Child Node. Contains group Encrypted files: Parent Node. Displays the total number of encrypted files. Without child nodes
Encrypted files: Parent Node. Displays the total number of encrypted files. Without child nodes
The numbering is done through special counters that increase as the groups are created. Each encryption engine corresponds to its own counter. The numbering starts from zero and increases by one unit per group. When a group is deleted, the associated number is also eliminated and will not be repeated with the creation of new groups.
To select a group of files, simply click on the desired node with the left mouse button. All files related to the selected group will be displayed in the grid on the right. On the Status Bar, as previously mentioned, data related to the selection will be displayed.
When accessing the selection of encrypted files, the grid configured to the right of the section provides numerous options related to the files, in addition to sending them to the decryption section. First of all, let's see how the columns of the grid are arranged:
 ID: the icon associated with the file is inserted in this column
ID: the icon associated with the file is inserted in this column NAME: the file name
NAME: the file name PATH: file name and path
PATH: file name and path SIZE: file size
SIZE: file size DATE: creation date
DATE: creation date
In the list of encrypted files, it is possible to make selections of single or multiple files. The data of the selection is displayed in the status bar of the program's main window. This is made possible by the Pop-up Menu described in the page of this guide entitled Work Environment in the paragraph Pop-up Menu.
From this grid, it is possible to send files to the section called Add Files in order to compose the list to be submitted to the encryption process. The submission involves one or more files, as described in the page of this Online Guide entitled Encryption and Decryption in the paragraph named The Decryption Process.
The section named Encrypted Files on the main page of the program is one of the most convenient functions that Speedcrypt offers its users, as it makes decryption processes related to the three engines provided with the project hierarchical, organized, and easily identifiable. With just a few mouse clicks, it is possible to start the decryption process and then restore the original files.







































