Process Encryption and Decryption Times |
After each Encryption or Decryption process, Speedcrypt generates a report that displays the duration times, in order to compare the various Encryption Engines and associated Compression Algorithms.
When comparing various Encryption and Decryption processes, it is important to consider those that include file compression. With the exception of the PGP Engine, which uses the Zip Compressor by default, it is possible to associate the compression algorithms present in the Speedcrypt Project or not.
The section in question is divided into two distinct parts. The first, located on the left and configured as a grid, displays the reports with various parameters related to the Encryption or Decryption process. The right-hand side, called Processed KB, shows statistics related to the number of processes, the total KB processed, and allows for manipulation of the list itself.
The section as a whole is easy to understand, well-organized, and visually pleasing. It is not related to the Status Bar, but it is partially manageable through the program's Main Menu. To access it, go to the Work Environment section and then to Encryption Time. The following options will then be immediately available:
 Export list: allows you to store the contents of the list in a file with the TXT extension
Export list: allows you to store the contents of the list in a file with the TXT extension Delete Item: deletes one or more selected items
Delete Item: deletes one or more selected items Delete List: delete the complete contents of the list
Delete List: delete the complete contents of the list
The grid of times related to the various processes is populated by a completely independent archive that has no influence on the parameters related to the encryption engines. It is therefore possible to delete individual values or the entire list without any danger to the decryption processes associated with them.
As previously mentioned, Speedcrypt creates a report for each Encryption or Decryption process that shows the time taken for each process in minutes, seconds, and milliseconds. In addition, some parameters with which the process was started are also displayed. Let's now take a detailed look at each column and its functions:
 ID: the icon associated with each process. A padlock closed when it is an encryption process, open if for decryption
ID: the icon associated with each process. A padlock closed when it is an encryption process, open if for decryption DATE: date and time the process was run
DATE: date and time the process was run STATUS: the type of process
STATUS: the type of process ENGINES: the encryption engine used
ENGINES: the encryption engine used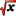 HASH: the HASH engine used
HASH: the HASH engine used CMP: the active compression algorithm
CMP: the active compression algorithm CMP: whether compression was used in the process
CMP: whether compression was used in the process DELETION: the deletion algorithm used in the process
DELETION: the deletion algorithm used in the process SIZE: the total KB of the process
SIZE: the total KB of the process TIME: the time taken by the process
TIME: the time taken by the process
The Report of Encryption and Decryption processes is an extremely useful tool for cross-comparing the various engines and algorithms used in the Speedcrypt Project. The execution times of a process are very important for planning the right encryption strategy. By analysing the Report, it is possible to determine which Encryption Algorithms and Compression Methods are the most efficient, and adjust the settings for future Encryption or Decryption Processes accordingly.
Once automatically generated by Speedcrypt in the appropriate grid, the list of processes can be manipulated at will before storing its contents in a text file. Let's see what options are available to the user:
 Export list to TXT File: allows you to store the contents of the list in a file with the TXT extension
Export list to TXT File: allows you to store the contents of the list in a file with the TXT extension Delete process: once the selection has been made, one or more processes can be deleted
Delete process: once the selection has been made, one or more processes can be deleted Delete List: delete the complete contents of the list
Delete List: delete the complete contents of the list
After making the necessary modifications to the list, it is possible to save its contents to a text file that can be consulted later to compare the various processes from the point of view of execution speed.
As previously mentioned, the Time of Encryption section is very useful to have a comprehensive and complete overview of the performance, in terms of speed, of the various engines and algorithms available in the Speedcrypt Project. By comparing the different processes, it is possible to plan the most suitable encryption strategy for one's needs.







































